Hack password using BRUTUS
(dictionary attack method)
INTRODUCTION:-A dictionary attack is when a text file full of commonly used passwords, or a
list of every word from the dictionary is used against a password database. Strong
passwords usually aren't vulnerable to this kind of attack. In the following
example, I will use Brutus, a very common password cracker, to show a dictionary
attack against an ftp server. Brutus is a Windows only program, but at the end of
this chapter I will list a couple more password crackers, some of which are made
for Mac, Windows, and Linux.
TUTORIALS:-
1. First the hacker would choose a target. In this case it’s my home
computer and the IP address for your home computer is 127.0.0.1 .
2. By going to ftp://127.0.0.1 I get a pop-up box asking for a username and
password.
3. Next the hacker would launch Brutus and attempt
to crack the password.
4. In the target you put the IP address of the website and to the right
select the appropriate option, which in this case is FTP.
5. The default port is 21 but some websites change this to make them a
little more secure. If you find out that the port isn’t 21, you can find the
right one by doing a port scan. We will get into this later in the book.
6. If you don’t know any of the usernames for the FTP server, then you will
have to get a list of the most common usernames.
7. For a dictionary attack you will have to choose the pass mode Word List
and browse and select the file containing your word list. You can get
some good password lists at
http://packetstormsecurity.com/Crackers/wordlists/
Below are
examples of what a username and password list might look like.
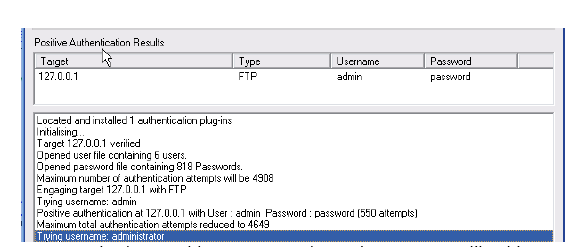
8. Once you hit Start the program will attempt to connect to the server and
begin to try all the possible combinations from your lists.
9. If you’re lucky, eventually it’ll get the right Username:Password
combination. As you can see below, it got the correct combination of
username – admin and password – password.
10. A smarter hacker would use a proxy when using a program like this.
What a proxy does is cloaks your IP address by sending your connection
request through another computer before going to the target. This is a
smart idea because as you will see in the image below, Brutus leaves a
huge log of your presence on the target server.
In place of the IP address 127.0.0.1 would be the hackers IP address.
Footprints like these get a hacker caught and into a lot of trouble with
the law.





1 comments:
for this attack which software we have to use
Post a Comment